|
You can see the meaning of the word when you point the word of this color.
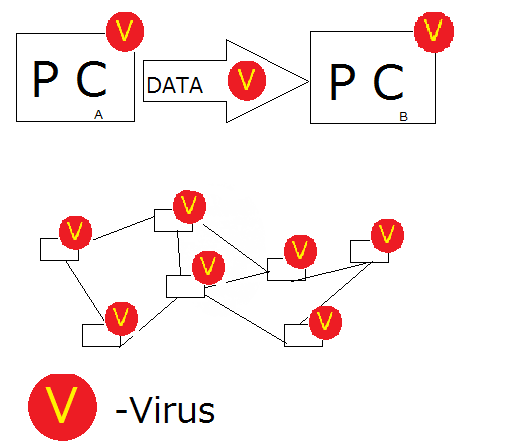
Progress of programDiversification of computer virusAt first, I will describe what computer virus is. In Japan, the definition of it is written in the Public Notice No. 952 by MITI (now METI). According to the notice, computer virus is defined as the ill program that has the function to infect itself, hide and attack.
First, the function of computer virus to infect itself is "the function to infect to other systems to copy itself by using functions of itself or system". This type can be seen in the old type of computer virus. That is to say the function that program copies itself increases itself. As this situation was like virus which caught by human, the ill program was named "computer virus". Next, the function to hide is "the function not to start attacking until the time when the recorded conditions were filled". There are two stages in computer virus same as human's virus: infection and attack. There are computer virus which start to infect and attack in the same time, but most of ones that have been damaged are not. Because advanced techniques are basically used in the latter. And also, as the advanced virus is so difficult to be noticed, such a virus is difficult to investigate maker, because route of infection is difficult to be known. This is the big advantage for hackers. By the way, the virus found by the anti-virus software are usually hiding one so it is basically harmless. Last, the function to attack is "the function to destroy program and data and to behave against maker's thought". This is the most outstanding function in ones for computer virus. According to the characteristic of virus, this is classified large. The program which has functions above is called "computer virus". Then, I will express about kind of computer virus next. First, there is virus to destroy - destroy particular files, break hardware, change way to display at its discretion, format hard disk arbitrarily -. This is the most notorious in the cases of virus and what might be so serious if the computer caught it. Though there are some books written this as "computer virus in narrow sense", we don't divide strictly into "computer virus in 'broad' sense", which contains "worm", "Trojan horse", etc.
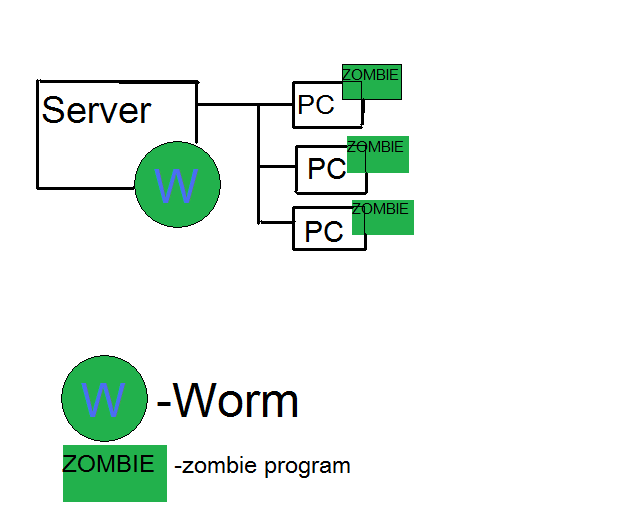
Second, there is virus called "worm" - which has functions to send mails attached virus, to send many empty mails, to reproduce itself in the field of LAN, etc. - Worm infects not only computers but also servers and starts attacking and reproducing itself. Sometimes such a worm is called "systemic virus". They make computer program called "zombie program" for computer device being client in LAN at user's discretion. And they made "zombie program" do destroy activity or steal personal information. The symptom of this "zombie program" is so similar to general computer virus, so it is thought as one kind of computer virus. However, the different point is computer virus can be deleted but "zombie program" propagates itself and produced again unless worm in server is deleted. I think such a property is reason why it is called "zombie program". Third, there is virus called "Trojan horse" - which destroys at the inside of the computer by acting game, convenient program, etc. and having users take in. The characteristic of Trojan horse-type virus is not to propagate and to be alone. Although we can say this is not computer virus from this characteristic, it is usually seen to be computer virus as vicious software. By the way, what is origin of "Trojan horse"? This comes from the unit used in Trojan War of Greek mythology. When Greek soldiers attack fortified city of Troy, they used big horse statue that can contain soldiers. Then, they left this horse in front of enemy's city and pretend to have withdrawn. Trojan citizens thought this is holy thing and cerebrated winning. But, at the night, Greek soldiers inside horse attacked city from inside of the city. Troy was fallen. This is origin of the name. What we can say from "Trojan horse" is that even if we high wall (=security), damage is caused by low consciousness of citizens (=users). (This can be said it is not example of "Trojan horse".) Beyond virus above, there is virus using macro, WSH, etc. Also, many compound viruses (e.g. which steal data and destroy file at once) has been found. Though virus security softs renew pattern files and take action against such cases, in fact, it is vicious circle by development of subspecies, virus generator, etc. To themes of same layer |
|
(c) 2010-2011 Team "Merit and Demerit of Information Technology" All rights reserved. Created by ez-HTML |