5th period: Advantages and Disadvantages -IoT-security-
IoT Security matters
<About Security>
IoT equipment is in a situation where "things" and the Internet are always connected because "things" generates value by connecting to the Internet and obtaining information.
Therefore, there is a very high risk that the damage will be increased in the event of a security attack.
In addition, it is difficult to think about "security" because the target is different by "things" connected by IoT.
<Security guidelines>
There are a number of different agencies and companies that share guidelines about the security mindset, methods, and risks of IoT.
Ministry of Internal Affairs and METI "IoT Security Guideline ver 1.0" Target: Service providers and users* Source: Ministry of Internal Affairs and Communications Information processing promotion organization, "Security Design Guide for IoT development" Target: Business operators* Source: IPA Information Processing Promotion organization
Some of them are for users, but most of them are on the developer side. What are the problems with the security risks of IoT? Let's think together.
Comparing IT and IoT devices
Does the security measures for IT products (PC, server, and mobile devices) that have ever been connected to the Internet are not acceptable to IoT devices?
<Comparing IT and IoT devices>
1. Life cycle Differences
IoT devices, such as cars and factory facilities, are often used over a period of over ten years, and the security measures at the time of development may be outdated over the course of their use.
In addition, IT equipment such as a personal computer had been taken measures such as a security patch, but the IoT device will remain in question whether the appropriate correspondence is done in the use.
2. Differences in relationship between people and equipment
Traditionally IT equipment was basically a role that people manipulated and displayed information to people.
In contrast, IoT devices operate automatically without the need for human interaction.
As a result,you may not be aware that there is something wrong with the IoT device, even if it is being used by others illegally.
3. Differences in the usage environment
There is a big difference in the usage environment.
Most of the traditional IT equipment was used in the environment where people live, such as offices, homes, hospitals and stores.
However, IoT devices are used in a variety of environments regardless of indoors or outdoors, and many people are not.
It is assumed that it is used in the vehicles, a farm and water, may be operating in a harsh environment for the equipment. In such an environment, it is possible to detect false alarms or damage equipment.
In this way, there is a difference between the use time, the environment, and the use method, and we think that the security of the IoT device cannot cope only by measures to the conventional IT equipment.
A wide variety of IoT devices
<Objects we should protect>
IoT has a variety of "things" connected to the Internet.Depending on what kind of "things" is connected, there is a difference in the importance and severity. Let's consider the example of "Home and IoT" that We studied for 2nd lesson.
What can be considered a security threat in a smart house if your house was a smart house?
-Access to the air conditioner by others without permission, the setting temperature is wrong...
-Unauthorized access to the refrigerator and tampering with the contents of the data,so AI promote the same menu every day...
These will not be such a serious damage.
But if it's a smart lock that has been illegally accessed and is unlocked without permission,what do you think? Also, if someone had taken over the webcam and looked inside the house...
In this way, the IoT in the same house has different information we should protect and severity.
It can become a very serious threat to human life if it is not only used in medical care, but also by means of traffic such as cars and runaway by malfunction or unauthorized access.
Security measures
So what should you do to protect your IoT devices from security threats?
We tried to think about security measures.
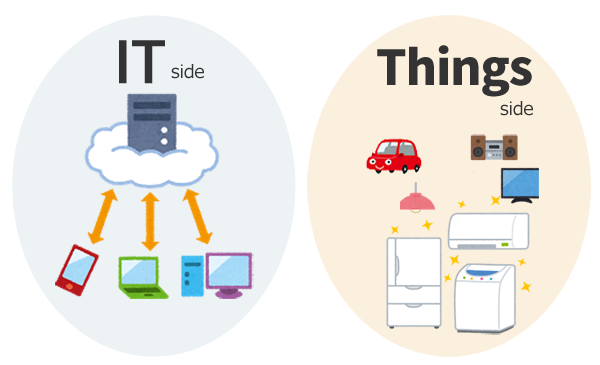
We thought that the security measures of IoT should be separated into two things: the Internet side and the things side.
On the Internet side, we should proceed with security measures while thinking like IT equipment. Then,we think that the things side should think individually by the kind of thing without lumping it to the IoT product. And we think each should do security measures from a different point of view.
For example, let's say that an automatic driving car is hacked into someone and starts a runaway.
 In this case, the security measures on the network side have been breached. In this case, there is a possibility of an accident and it is very dangerous.
For these times, I thought it would be a way out if there was another physical measure on the vehicle side.
In this case, the security measures on the network side have been breached. In this case, there is a possibility of an accident and it is very dangerous.
For these times, I thought it would be a way out if there was another physical measure on the vehicle side.
For example, when the driver can not controll, by pressing the button in the car without relying on the instructions from the network, the mechanism of braking and switching to manual operation is activated.
I think that it is necessary to have the mechanism which can physically control such a thing.
In this way, if you consider security by dividing into two perspectives, in smart houses,security measures on the Internet side should be given to one window that connects the house to the outside, such as a router in the house, and you should be able to think about measures that can be safely used individually for each thing.。
I think that it is more efficient and more advanced measures that the one IoT product does not measure both the Internet side and the things side,then we consider separately and should pursue the measures which specialize in the feature of the thing deeply.
Our approach
It is essential for developers, manufacturers, and equipment distributors to take security precautions, but what should we do to protect consumers? I thought about a specific solution that the consumer now could do.
- Select products that are equipped with an update or other support system when buying IoT devices.
- Update the Product frequently
- The initial setting is sure to be done by looking at the manual.
- Pay attention to set your ID and password (avoid using it or simple)
- Erase information when you discard your IoT device
- Implement security measures (such as encryption) of network equipment, not just IoT devices
The IoT is still new, and there is a possibility that the threat that we do not imagine comes out. I think it is important for developers, manufacturers, and consumers to take full action on security threats in their respective roles.
The disadvantages of IoT we think
①Threats of security ②Need to develop a law ③IoT products have a breakdown or lifespan
Security measures of IoT we think
We think that it leads to a thorough security measures to pursue the security measures each for each "things" which does not think in the lump sum with "security measures of IoT" because of various variety of IoT devices.
Thank you for your hard work. The 5th period: the advantages and disadvantages of IoT are up to this point.
The security measures of IoT are very important, so let's think about it together in the future. The next is finally summarized.





