The “Proof” of the safety of proof of work

Introduction-1, Hash Function
We use the operation of hash calculation as "lottery" of computer.
Hash calculation is an operation to convert given data into a character string consisting of 16
numeric characters and a total of 16 alphabets with numbers and 6 alphabets.

Since the character string to be converted is random according to input data, this hash value can be regarded as a lottery.
Let's define the "win" of the lottery as "the data whose two digits at the beginning of the hash value start with 0".
Then, the probability of getting around is equal to the probability of "assigning a
hash value whose first two digits are 0" out of random character strings, there are 16 kinds of characters,
so the probability is 16 × 16, That is, it will be one-fifth of that.
This probability decreases exponentially by returning the condition of how many first digits are equal to 0.
This is the "lottery" mechanism of computers.
Introduction-2, Fork
However, there is a possibility that this alone may give the right to malicious users the right to
record blocks containing illegal transactions.
Therefore, "branch" is going to happen in the blockchain.
When a different user writes different data from the outside in the blockchain while a good
user wishes to concatenate the blocks and calculates the hash, the block is not recorded immediately but extends as one "branch" I will.
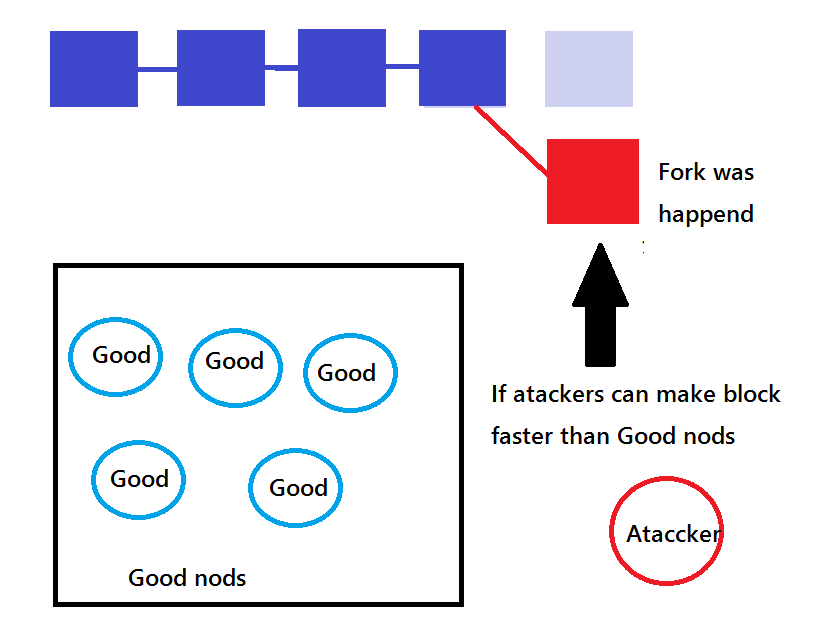
After that, the block connected by the good user is recorded in the blockchain as a new branch, so that two kinds of blocks are recorded in parallel.

Users who are divided into two groups resume hash calculation to connect new blocks to "branches" of each branch.
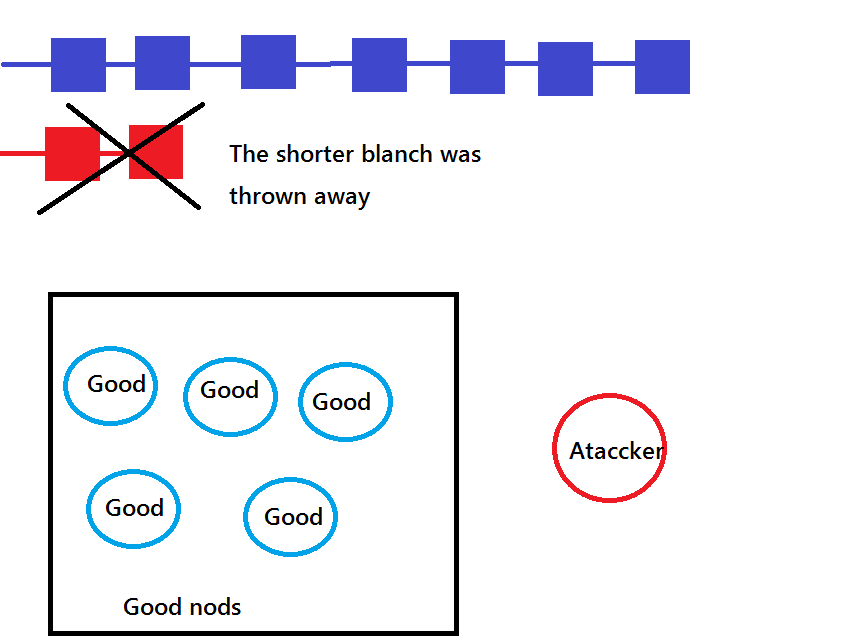
When there is some difference in the length of the two branches, it is decided that there was no shorter branch,
and the blockchain returns to the original one.
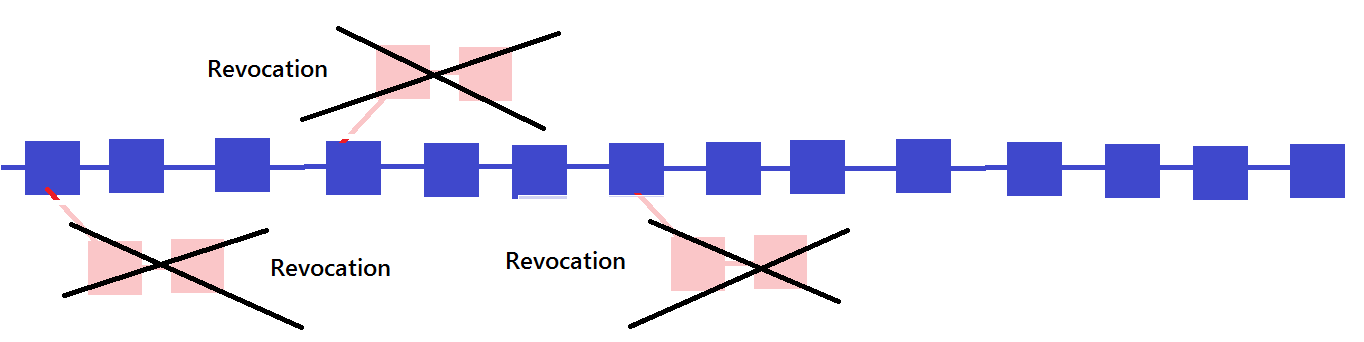
By doing like this, even if the bad late late luckily withdraws "around", it will be made not by the majority faction with high speed of calculation.
Let's do experiments at once, as you know the mechanism of hash calculation.
Purpose of The Experiment
Assuming that users trying to record illegal data in a blockchain connected by a good user assumed that the data had been tampered with, and by simulating with a pseudo blockchain system, verification of safety do.
What to prepare
Java runtime environment (personal computer)
A hash calculation program imitating a good user (called a good node)
A hash calculation program (called an enemy node) imitating a user who intends to register incorrect data
A program (called an observer) that records pseudo blockchains according to hash calculation
Procedure
(1) On the assumption that about 20% of the computers in the world attempt to tamper with the blockchain,
the program is started so that the ratio of the calculation speed of the good node to the enemy node is 9: 2.
(2) The good node and the enemy node perform hash calculation using data imitating the transaction data and random number, respectively.
(3) Hash calculation is performed, and one whose sixth digit of the hash value starts with 0 is regarded as "around",
and transaction data is recorded through the observation program.
(4) The good node and the enemy node add the block in parallel, and if there are five or more differences in the
number of connected blocks, judge the longer one as the correct block and discard the short data.
(5) Record how blocks are connected until 100 blocks are connected, and this is repeated ten times.
Situation of Experiment
In the experiment, I visualized how blocks are connected using Java Applet.
Results of The Experiment
As a result of the experiment, the number of times the branch occurred until 100 blocks were connected was at most 10 times, at least 6 times, on average 8.6 times. The median was 7 times
In addition, the number of blocks connected to the branched branches was 14 at the maximum, 1 at the lowest, and 2.5 on the average. The median was 2
The enemy node never succeeded in recording illegal transaction data.
Consideration
Experimental results show that even if the computation speed slower
sometimes succeeds in hash computation, in most cases it is discarded by good nodes while connecting two or three blocks.
This time it assumed that 20% of computers in the whole world attempt to tamper with the blockchain,
but in fact it is difficult to secure a calculation speed comparable to 20% of the computer of the whole world even with supercomputer,
Others
When the ratio of the number of good nodes to the number of enemy nodes is set to 6: 5,
there are cases where an illegal block was recorded despite the fact that the number of good nodes is larger.
This is because the ratio of the calculation speed was adjusted by the number of program activation,
so the ratio of the calculation speed was not strict, and the number to be calculated at once was not
sufficiently large and it was difficult to converge to a mathematical value It is thought that it was
caused by setting the frequency of subtracting "around" of the hash value higher than the actual value for the experiment, etc.
Summary
The paper published by Satoshi Nakamoto, the founder of bitcoin, says,
"If you have a computing power that is high enough to break the Proof of work system, it is better to do all
the approval work and gain profit from mining I will do ".
Also, once you know that the fraud countermeasure is incomplete, the cryptocurrency loses its trust
and the value of the cryptocurrency you got by tampering is lowered.
From these two things, falsifying the cryptocurrency in order to raise the profit will not fit.
Thus, by combining various advanced technologies, the cryptocurrency can maintain its value as a currency.


