WEP crack
Why do We Do
Has been described as dangerous to WEP in the "Wireless LAN Security", so anxious over not frame will realize how dangerous it really, whether it is possible to analyze We really an experiment to analyze the WEP key actually made.
Do you not feel a longing to hackers or about once ... if you know a boy is not wanted to do the cracking of curiosity never.
Is it good to do like it?
I think whether it is not the first and I thought, "Is it good to do such a thing." However, there is no problem to do so this time hacking into their wireless LAN access point.
However, it is illegal to crack a wireless LAN access point for other people.
Experiment environment
As I can not crack the AP of others, I have prepared the environment for performing the cracking.
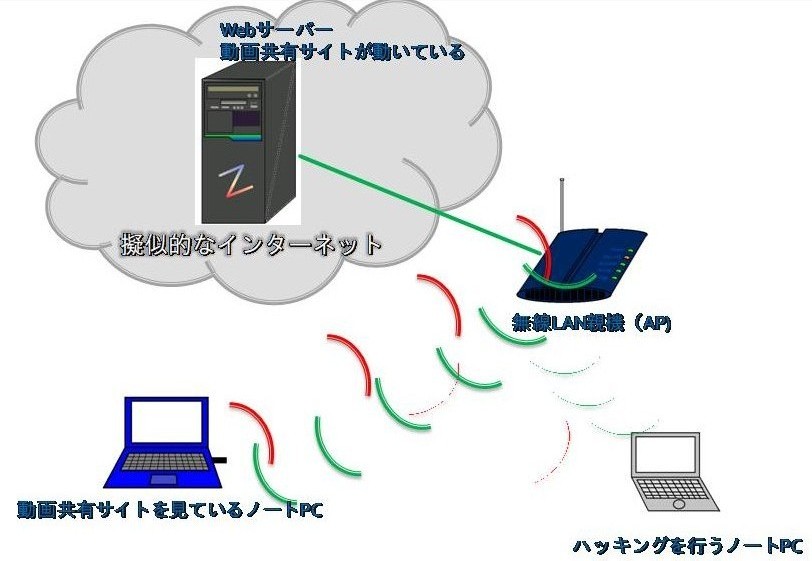 These PC's, the state has been reproduced laptop to connect to the Internet using the wireless LAN in a pseudo manner, looking at the video site. Please do not worry about has been greatly simplified because there is no technical skills to us and the unimportant portions of the Internet.
These PC's, the state has been reproduced laptop to connect to the Internet using the wireless LAN in a pseudo manner, looking at the video site. Please do not worry about has been greatly simplified because there is no technical skills to us and the unimportant portions of the Internet.
Speaking of the situation why I chose that site has seen this video, I will not go to analyze the password for the wireless LAN will not intercept communications of a decent amount. It was a video site that was chosen there is exchange of a large number of packets is performed.
Equipment description
 I have experimented with this feeling. I'm cool with doing an activity like something seriously.
I have experimented with this feeling. I'm cool with doing an activity like something seriously.
Web server
In the production of your PC microcomputer Hongo, running the web server to deliver the mock video site. (OS is Ubuntu Web Server Apache)
Wireless LAN router
Within this network, it is a machine that can make communication between the personal computer and the Web server, perform the wireless LAN communication.Model is BUFFALO AirStation WHR-300. I got to go to buy this model because for this experiment to Bic Camera in Ikebukuro, it was cheap.
This has to do is set loosely hacking, this security, this model does not mean that I, dangerous. The danger is that if the wrong settings other words, that the same can be said by any state on the model.
As an aside, to have been asked about this wireless LAN router and "GB? What is this" junior counsel (a different person and coach). It was when I was told to put away for a cultural festival that ends well, I just tossed the club room with equipment. I wish there was an external hard drive made ??by BUFFALO to the staff room for example it says.

Laptop View video site
Mini laptop made ??by Acer's own junior Hongo microcomputer unit. Which was referred to as the so-called netbook, I was connected to the wireless LAN in the cordless handset manufactured by BUFFALO wireless LAN connection of USB. The light ... so so hard to be out on-screen keyboard is small and only has merit I was hard to lose the IP address for some reason when you wake up from standby.In Windows XP, OS, the browser is Google Chrome.

Laptop to do hacking
Laptop personal belongings of the leader. The model in Panasonic CE-T5, quite old model, who stood nearly five years since its release. Built-in wireless LANOS is BackTrack5. In the OS for the penetration test is performed to test whether there is actually hacking the security issue, OS is, There are a lot of hacking tools. This time I use the one that came about the supplement to a magazine, you will be able to use free of charge by anyone because they are distributed on the Internet, the use is reasonably necessary knowledge.

Hacking procedure
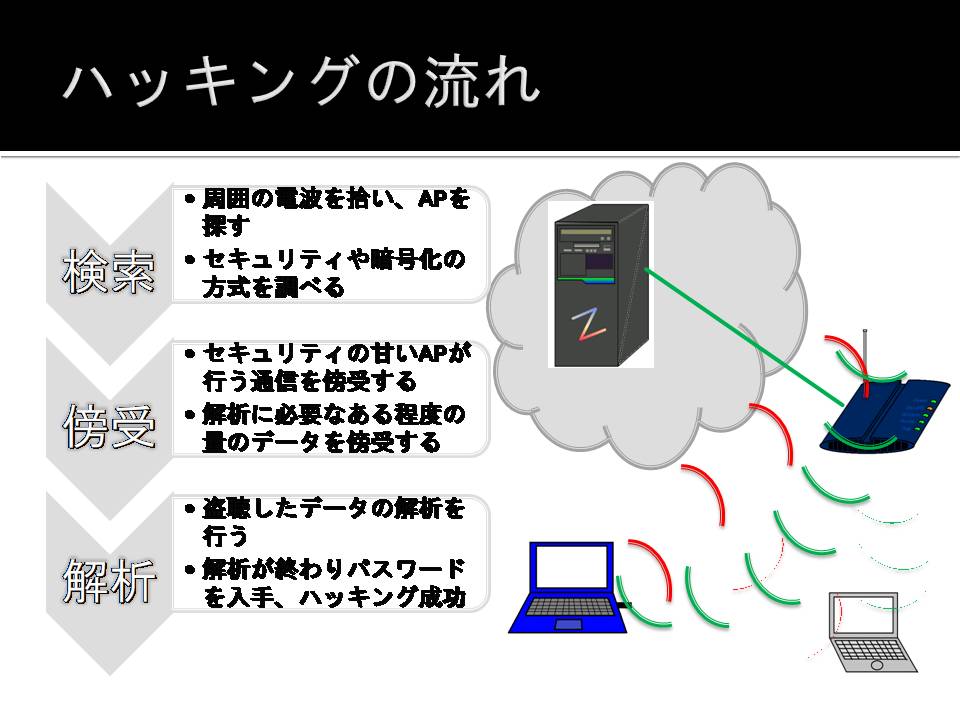
Hacking Tools
Using (tool that helps you make better use of the Aircrack-ng suite) Aircrack-ng suite and the (county tools for hacking wireless LAN), Gerix of its front end. I've run a laptop to do the hack that was introduced in this item of equipment described.
This target
In "hongomc" SSID of the wireless LAN access point was provided,
It is a "hongomc1n7u9q" The WEP key of wireless LAN to be analyzed in this hack.
If successful, the analysis of the WEP key, you will be successful experiment.
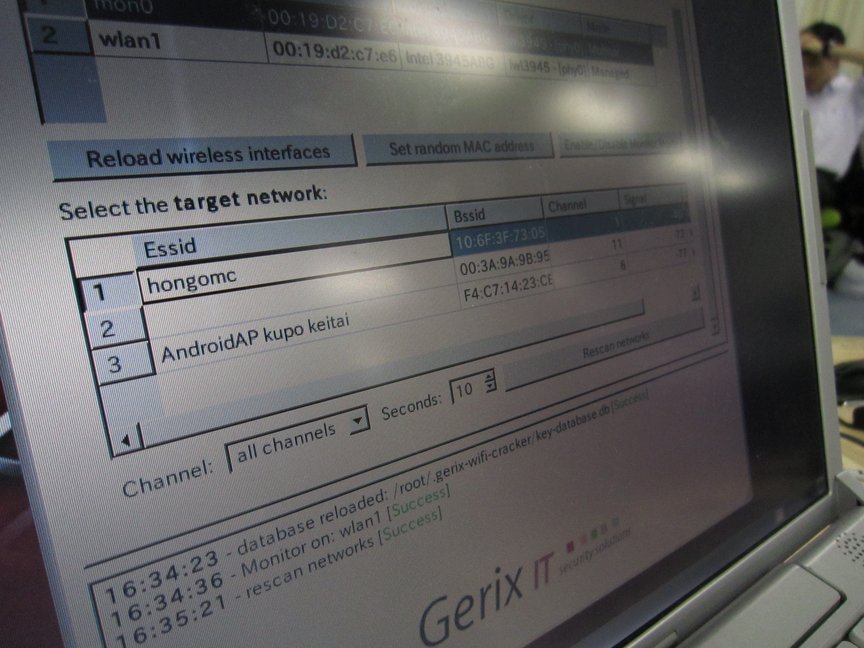
Search
I found a wireless LAN access point called "hongomc" Do you see? I have also found that the WEP security is that it can not see the photo.
Intercept
I have to intercept communications. See video site on a laptop, so that a lot of data to play the video stream. A little time consuming because you need to intercept the data to some extent.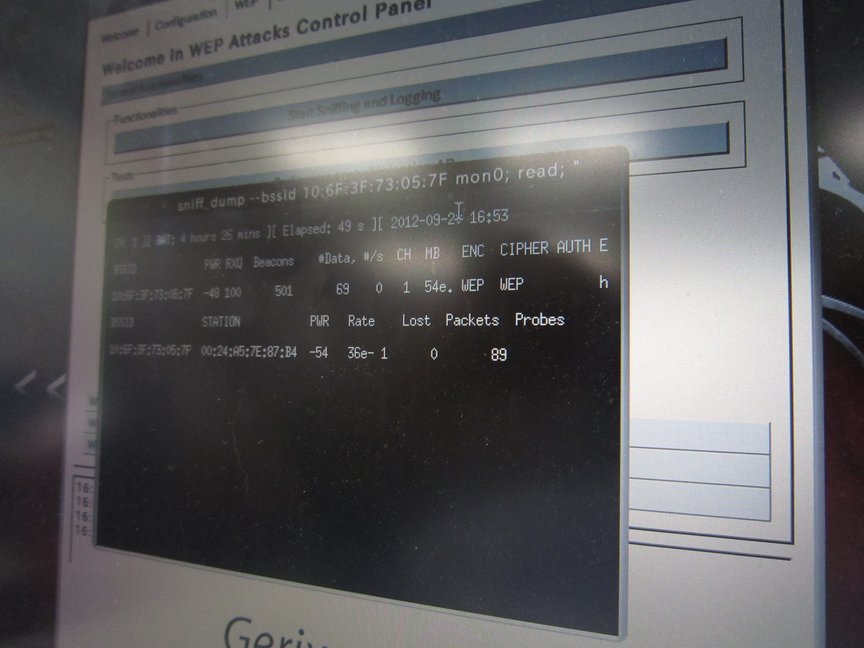
Analysis
Since it is possible to intercept a certain amount of data, we analyzed. I wait anxiously to finish the analysis.
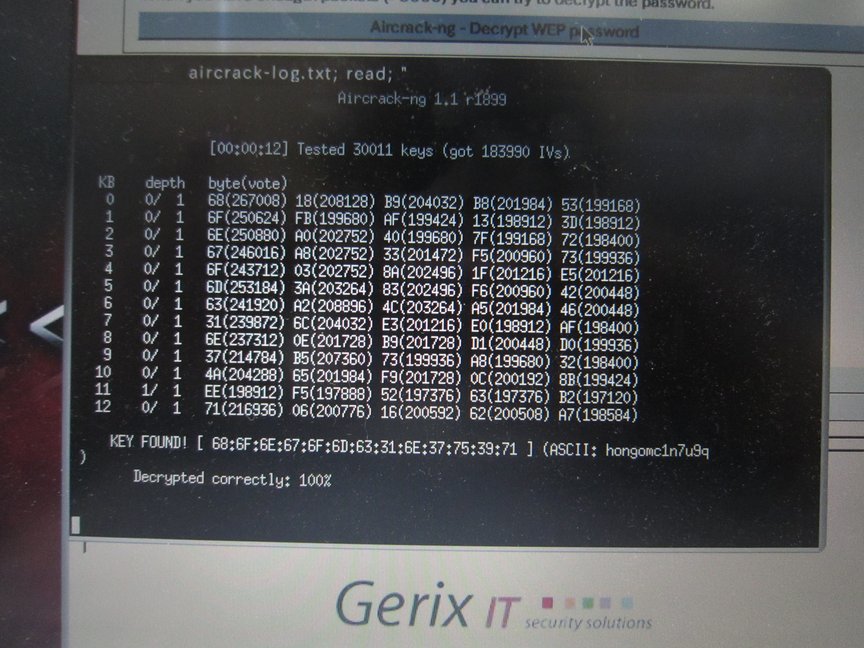
Analysis was successful!
Beyond the "KEY FOUND!", And "hongomc1n7u9q", WEP key wireless LAN access point is displayed.
Experiment is a success. I was able to analyze the WEP key.
Last of all
Analysis is completed, several tens of seconds while you are taking pictures intended to collect material for 12 seconds, click the start button on the analysis in the feeling, I've been disappointed According to the log. I would have taken time to prepare or just how I bought the book, you can build a Web server, you can create something like a video site, and I bought a LAN or a wireless access point ...
Using a combination of the current WPA2 authentication and AES encryption, effective analysis method because it is not found at present, you can use a wireless LAN quite safely.
However, there is something I do not have day-to-day progress of the PC to be used for performance analysis and analysis of technology and encryption scheme that absolutely secure encryption. It might be a good day will come to be decrypted because there would be any cryptographic, and always know the following information about the encryption technology.
Bibliography
続・ハッキングの達人 ハッカージャパン編集部(編) 発行所:株式会社白夜書房
